After a long time, when I checked broken links and fixed them, I got an error about the size of the uploaded file. I haven’t changed the setting in php.ini about file sizes from before. I thought why. At sometime in the past I set them as below, because I wanted to prevent large files uploading from someone.
post_max_size = 8M upload_max_filesize = 2M
So I built an intra FileZilla server with FTP over TLS, and I used it for my articles’ images.
I haven’t noticed this trouble until now, which tells me that I didn’t do anything other than updating server software after changing to a Windows10 server. 😅
So, at this time, I’m going to build a FileZilla server.
Step1 Download a FTP server software from FileZilla site. FileZilla Server Download
Step2 Install the downloaded program on the server machine. I left the default except for the installation directory.
Step3 FTP Server / Security settings.
I am using the Let ’s Encrypt certificates for my web server, so I will also use them for the FTP server. The key.pem and cert.pem are in the md directory of Apache.
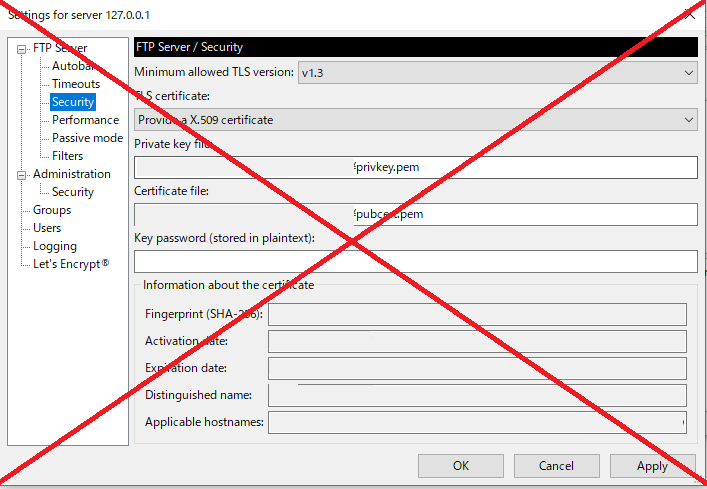
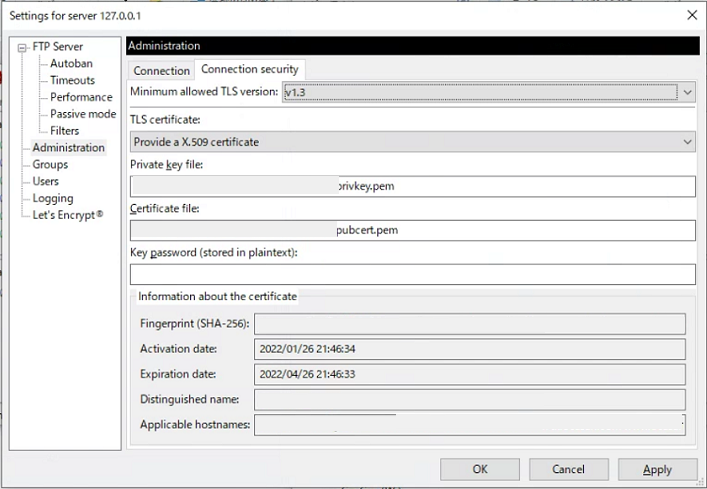
Addition: Today (2022.Feb.20), I noticed that FileZilla Server was updated to 1.3.0, and Security Tag location was replaced into Administration area.
Ref URL : Let’s encrypt – how?
Step4 Set users. But only me this time again. I also set a password for accessing as a client.
Step5 AS I need a permission by Windows10 Firewall, I go to “Windows Defender Firewall” >> “Allow apps or functions through Windows Defender Firewall” from Windows10 Control Panel. Now “Allow another app” button isn’t grayout, so click it. By the “Browse”, add filezilla-server.exe of the FileZilla Server folder.
Ref URL : The method about Windows 8 is written at the bottom.
Well, that’s it.
By the way, I got the following errors on the server log, when I disconnected as a user from Client Software.
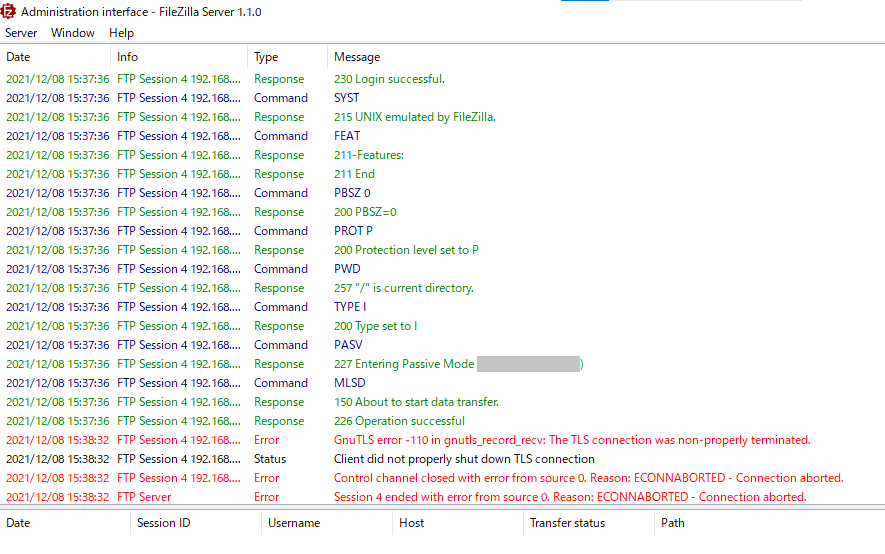
After surffing the Internet, I find out Trac has a comment from Tim Kosse that is ” Completely harmless, safe to ignore if there is no ongoing activity. I’m looking into a way to suppress these messages during periods of no activity.”
My FileZilla Server is on Windows10 Home x64 version 21H1 19043.1348 and version 1.1.0.
FileZilla Client version is 3.56.2.